How do you obtain network security? We explore the different options to help you avoid intruders stealing your information or eavesdropping on your network
How to improve your network security
The moment you start sharing information, you also risk sharing it with the wrong people. And since a network is essentially a flow of information between two or more devices, you could potentially face a network security breach any time you exchange something.
What is a secure network connection and what can you do to secure your setup? A secure network is any type of network that has security measures in place to protect from unwanted intrusions.
Every network is vulnerable to intrusions, but with the right security protocols, your network becomes less prone to attacks. We share our best and most essential tips on what to do to ensure a secure setup.
Perform updates regularly
Check for firmware and software updates regularly on all network components. Stay curious about new security features that could better your current setup.
Set a strong defense
To prevent anyone from stealing files on your network or eavesdropping, set a strong defense.
There are many next-generation firewalls (NGFW) that integrate Advanced Malware Protection (AMP), Application Visibility Control (AVC), Next-Generation Intrusion Prevention System (NGIPS), and URL filtering. As the threats to your networks grow more advanced, so should the firewalls you set up – take a look at all the benefits of NGFWs here.
MAC address restrictions
Every device that’s connected to a wireless network has a unique MAC (media access control) address. Knowing the MAC address of different devices allow you to set a limit on what devices may access your wireless network. Just find the MAC addresses on each device you’re using and enter the addresses in the list of allowed addresses on the wireless access point.
Our new device, Airtame 2, comes with the printed MAC address directly on the device and box, making cataloging of the MAC addresses even easier.
Read more: How networks work
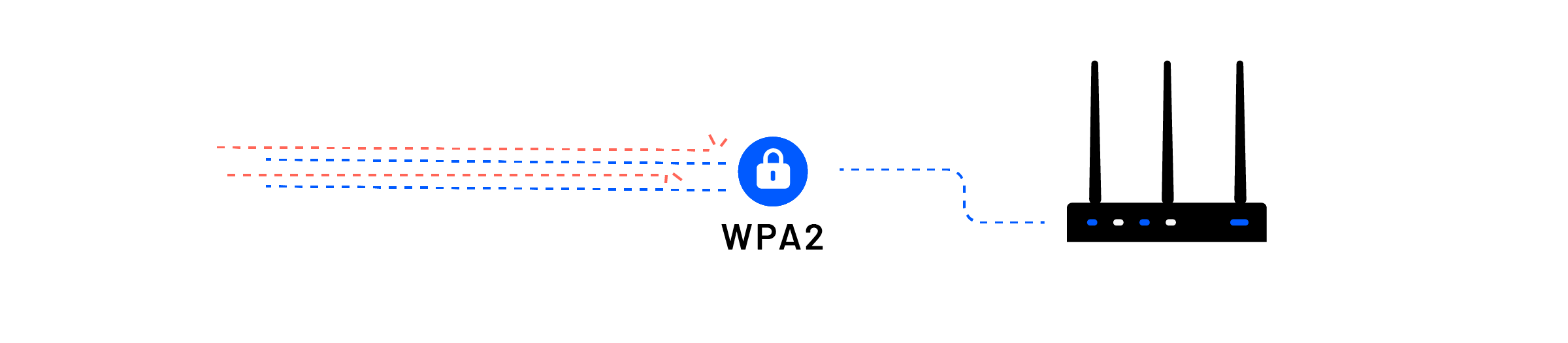
Authentication protocol
WiFi Protected Access such as WPA2 should be set up on your wireless router along with a password. WEP and WPA are now considered outdated, so make sure you’re up to speed with the new protocols.
WPA2 is essentially the set of rules that allows a host to authenticate to the network. WPA2-Personal states that a host/endpoint must know the preshared key to authenticate, thus making it difficult for intruders to piggyback on your network.
Broadcast SSID
Networks all have a name known as the SSID (service set identifier). Most likely you’ll see the ID broadcasted so that all wireless devices can select the network and connect.
If the wireless device doesn’t know the name of the network, then, of course, it can’t connect to it either, and that could be the protection you’re looking for. If you turn off Broadcast SSID, then your wireless network won’t broadcast its ID for client devices to find and connect to.
SD-Access
SD-Access (Software-Defined Access) can help you enable or disable network access for any user or device, to any application. It’s a great way to control who gets access to your network.
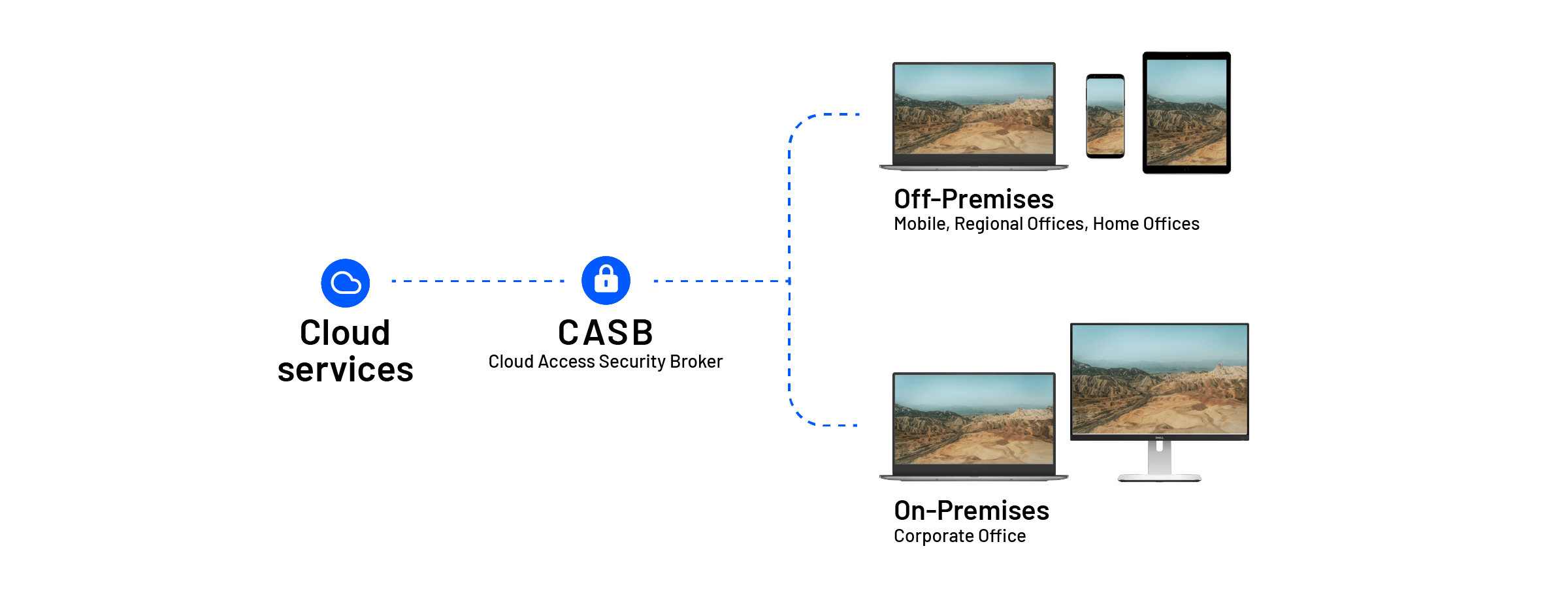
CASB
A CASB tool (cloud-access security broker) identifies threats in the cloud and protects against intrusions with a DLP (cloud-data loss-prevention) engine. With more and more information stored in the cloud, you need security measures that stands between your on-premises infrastructure and cloud applications and stops threats at the gateway.
Secure your network physically
While it’s imperative to secure your cloud applications and access to your network, it could be helpful to secure your network physically as well.
Why is that? Just as hackers, bots and viruses can seriously harm you if you don’t set up a firewall, intruders in real life can run away with your hardware or plug in a wireless router that gives them access to your network.
If you secure ports and outlets, disconnect the ones not in use or simply hide them away, then that shouldn’t happen as easily.