Airtame makes continuous efforts to protect the confidentiality, integrity and availability of the confidential information and personal data of employees, customers and vendors. As part of these exercises, Airtame will respond promptly to investigate, contain and mitigate any security incident that could lead to a data breach following the internal procedures intended for that purpose. If a data breach occurred, a notification will be provided to all the affected individuals and/or data authorities in accordance to applicable contractual and legal requirements.
To clear out the scope of the policy, Airtame offers the following definitions:
Airtame maintains a Security Incident Response Plan based on guidelines from the National Institute of Standards and Technology’s (NIST) Computer Security Incident Handling Guide.
As part of every employee responsibilities, immediate notification of any actual or suspected data breach must be reported without undue delay to the Information Security team. This will trigger the different processes described in the Incident Responsible Plan in order to determine if the reported incident actually involves a potential data breach. In case of a data breach, the plan defines the measures required to manage the incident and prevent further damage.
In this regard, a data breach can happen in various forms so every case and measures to be taken will be assessed on an ad-hoc base.
Following the Security Incident Response Plan , the Breach Notification Team (BNT) is responsible to handle the internal and external communication if a data breach has been discovered. In the meantime, the Information Security team will work on containing and mitigating the incident as defined by the process while the CFO, as legal advisor, and the rest of the team follow the Data Breach Notification Process in order to determine if a notification of supervisory authorities and affected data subjects is required.
Airtame in its role of data processor commits to a notification via email to affected data controllers -customers and/or partners-, specifically to the primary business contact registered upon contract signing, as soon as possible but no later than 72 hours of reasonable suspicion of a Data Breach, following GDPR guidelines. If there is an operational impact, an update can also be seen on https://status.airtame.com/.
Airtame in its role of data controller commits to a notification via email to affected Airtame employees and customers/vendors/partners, when acting as data controller with regards to their employees’ personal data, as required by applicable law and following the Data Breach Notification Process.
This website contains security information and resources related to Airtame, its products and services.
The CSA Security, Trust & Assurance Registry (CSA STAR) is one of the industry’s most powerful programs for security assurance in the cloud that encompasses key principles of transparency, rigorous auditing and harmonization of standard, helping customers and potential customers assess the security level of cloud offerings.

CSA STAR Level One self-assessment (Consensus Assessments Initiative Questionnaire, CAIQ) was submitted in order to provide answers regarding Airtame information security posture.
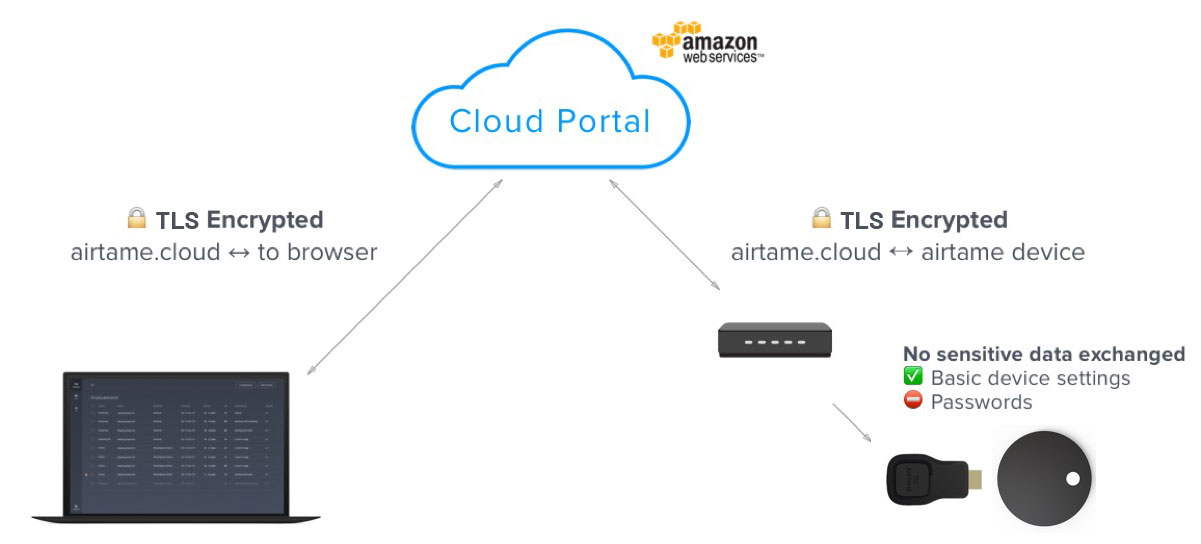
The Airtame Cloud platform is only accessible using HTTPS on TLS 1.2 or higher. Likewise, Airtame’s infrastructure uses encryption methodologies whenever our infrastructure components need to communicate with each other via public networks. Internal infrastructure traffic will always be routed through an internal and secure channel and firewalls are deployed between the sites to filter traffic accordingly.
User passwords are salted and hashed using bcrypt. Likewise, customer information is stored in our production database, which is encrypted using AES-256.
The Airtame Cloud solution is hosted on Amazon Web Services for a secure, reliable, and scalable solution, specifically in Frankfurt, Germany. AWS is a multi-certified datacenter provider, including ISO 27001:2013 and SOC 1, 2 and 3 reports. Further information about AWS security posture can be found on their website.
All communication between a user’s device, the cloud platform, and Airtame devices are encrypted, as a minimum, with TLS 1.2 (Transport Layer Security). Communication between the Airtame device and Airtame Cloud uses standard WebSocket communication established by the device.
If you want to know more about how to securely integrate your Airtames into your network, check out our most recommended setup.
Note that the Airtame devices don’t route streams via the Internet and do not in any way capture or send streaming information, so you can be sure that the video feed of your screen never leaves your network. Likewise, the stream itself is encrypted by your own WiFi network, which means that an attacker would first need to hack into your network and also reverse engineer Airtame’s Streaming protocol before they could see anything.
For those users wanting to use the “Screens” feature where one can get an overview of their Airtames’ home screens, there are some additional facts to layout about what happens with the images captured of a device’s home screen:
More details about how Airtame protects your information, including our PIN code feature or how physical security was taken into consideration, can be found in the following article.
The customer is responsible for user management within the Airtame platform. Access roles and rights within the application are predefined. Airtame cloud has 6 levels of user roles: Owner, Administrator, Content manager, Device and content manager, Moderator and User. There can only be one owner of an organization who holds exclusive rights to delete the organization account, once all other users have been deleted, as well as the ability to move account ownership. The administrator role gives full access to all functionality of Airtame Cloud, including being able to invite new users and edit user roles. An administrator can’t delete users, so the Cloud Owner is the only one who can delete other user’s accounts if they leave the company. In case something happens to the Cloud Owner, the customer can contact Airtame Support which can escalate this internally to manually change the Cloud Owner when needed.
You will always have the opportunity to enable SSO via OAuth 2.0 authorization protocol, currently available just through Google and Microsoft accounts. This way, you and your users won’t need to remember any extra password but use the same account you are already using within your organization.
Prior to employment, candidates will be assessed and checked on their background, considering the position they will hold and the applicable law and regulations. Employees will be made aware of security threats and best practices during onboarding as well as on an ongoing basis, including our internal monthly events. All employees are required to sign a Confidentiality Agreement included in their contract as a condition of employment.
To ensure the protection of information within our network, a 2nd generation firewall is installed with Deep Packet Inspection (DPI). Likewise, Intrusion Detection Systems are running to detect any anomaly so the team can take action, together with the AWS Web Application Firewall that protects our platform.
On the other hand, Airtame uses industry standard endpoint protection which relies on signature and heuristic detection.
Several kinds of logs are used to troubleshoot and monitor Airtame Cloud platform and applications for abnormal functional patterns, suspicious behavior and other activities that might result in non-compliances with the current Information Security Policy and/or existing legislation.
Likewise, if you need to troubleshoot either your Airtame devices or your Airtame application, you can always access their logs following the guides available on our Support center.
This process is consistently implemented within all phases of development. To continuously assure a reliable and secure product for our customers and partners, Airtame has its both cloud platform and devices tested for security vulnerabilities internally. This is done through quality checks, peer reviews and ‘bug hunting’ sessions, where our team of developers and quality engineers try out the new features to discover if the application or the products are not responding as they should before each release.
Likewise, security scans are also performed through automated and manual source code analysis during each build in the CI/CD pipeline, which helps to detect potential security defects in code prior to production release. Our Cloud platform is also scanned daily for vulnerabilities.
Reports of our vulnerability management program cannot be shared due to confidential reasons. If you are interested in reporting a potential vulnerability, please visit our Vulnerability Disclosure Policy.
Airtame is committed to the security of both our cloud platform and devices. Therefore, we acknowledge the key role that independent security researchers play in protecting the Internet and, because of that, we welcome them to disclose any vulnerabilities found directly to our team so we can verify and address any potential issue reported.
This policy describes how Airtame engages security researchers and the different considerations that need to be made when reporting a security vulnerability in a responsible way, including what is allowed and what is not allowed. If the policy is not followed, the chance of response to a vulnerability report will be reduced, which would also influence the possibility of getting a mention in our Hall of Fame or a bounty, in case applicable although not guaranteed -it depends on several factors including then-current budget, severity of the vulnerability and previous reports and acknowledgements.
If you’ve discovered a security vulnerability that you’d like to report, please send an email to security@airtame.com with the following information:
Due to business needs and engineering priorities, Airtame will need reasonable time to address any reported and verified vulnerability. Likewise, the reported vulnerabilities will be handled according to their severity and ease of exploitation. In this regard, we will be as transparent as possible and let you know about the status of the fix.
When trying to exploit a potential vulnerability, you must always take into account the following conditions: