Ever wondered how networks do their thing, and connect you to the wider world? We wondered too! Here’s our forensic research on how networks work
Ever wondered how networks do their thing, and connect you to the wider world? We wondered too! Here’s our forensic research on how networks work
We’re living in an ever more connected and technology-driven world. What’s keeping us connected, among many other things in life, are the computer networks that allow us to share information.
Regardless of whether we’re sharing information with our local communities or broadcaster our latest video blog across the globe, it’s the computer networks that interconnect our lives, interests, the digital signage we see and the businesses we care about the most.
Yet the idea of a complex global network of interconnected computers often escapes a lot of us. What exactly is a network and what can we expect to see in the future when it comes to networks and how we share information?
In this article, we cover all of the basic information about computer networks that you could want to know.
A network is a group of two or more computer systems or other devices, like Airtame, that are interconnected together for the purpose of exchanging data. The data shared over computer networks allow us to:
Think of it as networks sharing resources. Besides files (documents, images, music files…) or the same printer, networks can even provide a stream of information, like the information we send to the Airtame device with constant video and sound.
There are two types of networks; wired and wireless. They each come with both pros and cons. A wired network connection is the most secure and reliable choice for a stable internet connection. On the other hand, wireless connectivity gives you the freedom to move around and not stay tethered to the cable.
Sharing of files is a lot easier when you’re going wireless. The transfer time may be slower, but at least you don’t have to hook up to the other device with a cable. And when we’re at the point of cables, there’s tidiness of going wireless versus the cabled mess you often find in many work environments.
The setup of a wireless environment is far more hassle-free than a wired one. And as continued advancements make the wireless network technologies gradually more secure and speedy, you don’t have to worry as much about those issues either.
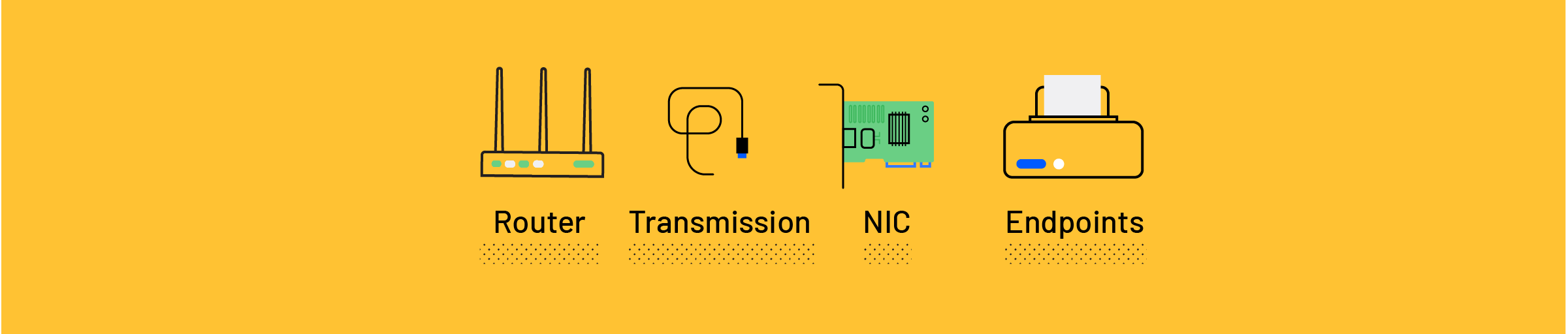
When you share something, like an email, that message is comprised of data packets that travel across the network. All files are broken down into data packets (1’s and 0’s), and data packets are created in “Internet Protocol (IP) transmissions” for data that navigate the Web and other types of networks.
Each packet is wrapped in a header and footer, that contains the information of what kind of data is inside, how it fits with other packets, where it came from and where to it is sent.
Different packets from the same message don’t always follow the same path, because that would slow the message down. Once the data packets arrive at the destination, the receiving unit assembles the packets and recreates the message.
Sounds abstract? Here’s an analogy that helps illuminate it. Imagine mailing an entire car to someone by packing each component into its own box and mailing them with a destination address and, in case it can’t make it, a return address.
It’s the same principle that applies to data packets, it’s just a little less cumbersome than mailing a car…
A wireless local area network (LAN) uses radio waves to connect devices (your laptop or smartphone) to the Internet, to your preferred network and the applications you use. When you connect to a WiFi hotspot, you connect to the wireless network it belongs to – could be an airport lounge or your favorite café.
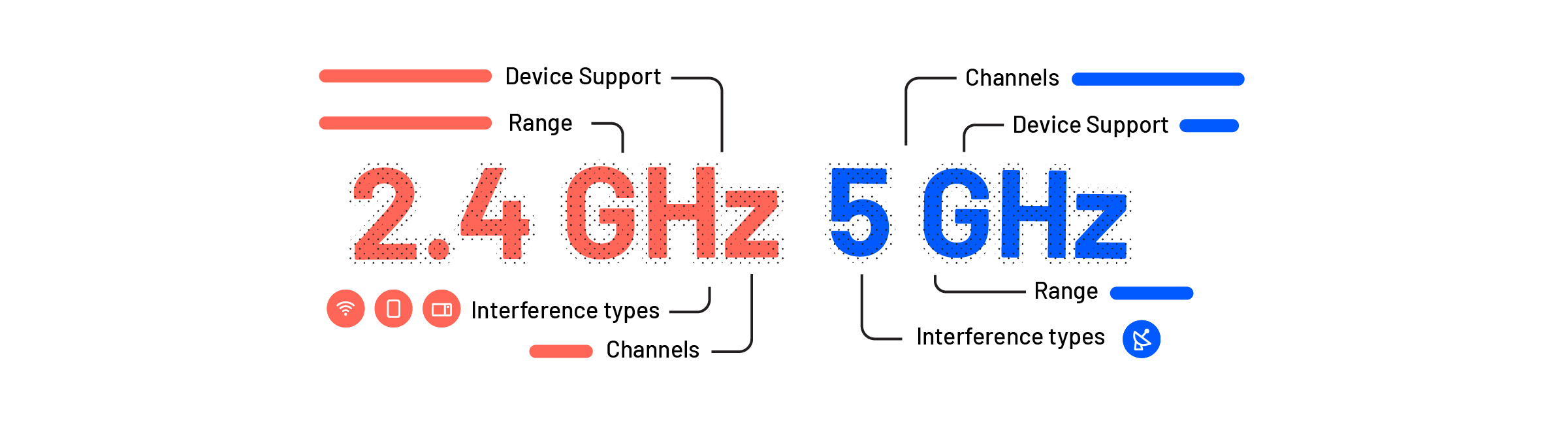
Because WiFi is an electromagnetic wave, it can have different frequencies (the amount of times the wave repeats, up and down, during a period of time). To avoid interference, two frequencies bands are used. They are 2.4GHz and 5GHz (1GHz = 1,000,000,000 Hz = 1,000,000,000 repetitions in 1 second).
“Channels” are the smaller variations of the frequencies that add a few more repetitions to the electromagnetic wave (e.g. 2.4GHz on channel 4 = 2.432.00.000Hz).
*Interesting fact: Ultra-high channels of 5GHz are banned in Europe because they’re frequently used by the military.
**We recommend using 5GHz with Airtame.
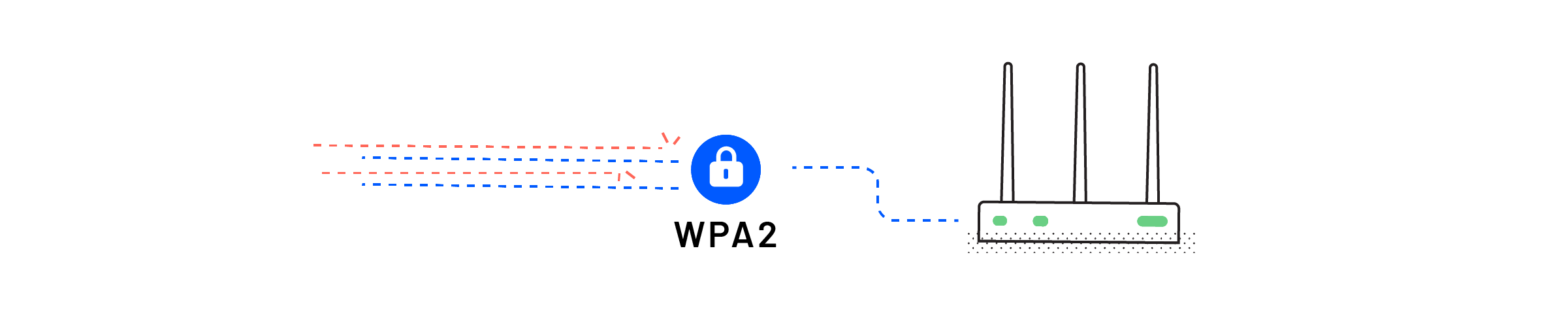
Your data is valuable, and having something valuable can make you more susceptible to theft.
In other to protect the confidentiality, integrity, and availability of your data, conforming to security standards will bolster your security posture and leave your data and your networks safe from malicious entities that exist online.
Depending on what the network is used for, it may need to have some rules applied so that people can’t access other computers, files or the network itself.
Wireless Authentication Security is the security that allows devices and people to prove that they’re supposed to have access to the network.
You can protect your network in a variety of ways, from having user certificates to having a known, pre-shared key (PSK). The methods vary but the main types are:
Not that long ago, we needed a dial-up modem to access the Internet. We have a lot more mobility and flexibility nowadays, and who knows what the future will bring in terms of more freedom? Or perhaps restrictions thereof. We take an educated stab in the dark at what’s next for networks.
The mother of all networks, the Internet, has also changed a lot in the past, and it’s sure to expand even further in the future. But will it be similar to what we have right now or could it possibly change to something completely different?
Cyber attacks are on the rise, and we can’t be sure that the Internet will withhold against increasingly powerful charges. Our guess is that either the Internet will improve vastly to withstand such attacks, or it will crumble and lead to a massively controlled security situation of Big Brother proportions where no ordinary cybercitizen is safe from scrutiny? We hope it’s the first.
Yes, we have a lot more mobility these days. Just think of your smartphone, essentially a small computer with as much power as one. Software Defined Networking, or SDN, is a cloud-based software that manages a network from one central point – and can really help with the desired mobility.
The architecture is more easily manageable and improves network performance, which is ideal for all of the high-bandwidth, dynamic nature of today’s, and perhaps the future’s, applications.
You may have heard the expression “Internet of Things” or IoT before, and no doubt you have come into contact with it.
In short, IoT is the network that links together smartphones, home appliances, vehicles and many other items embedded with software, connectivity, sensors etc. Because they’re linked together, all of these items can connect, collect and exchange data – and be controlled by you.
As more mobile devices, wearables, and other smart devices take over personal communication, managing traffic via fixed routers will not make as much sense as the devices communicating directly with each other and the Internet directly.
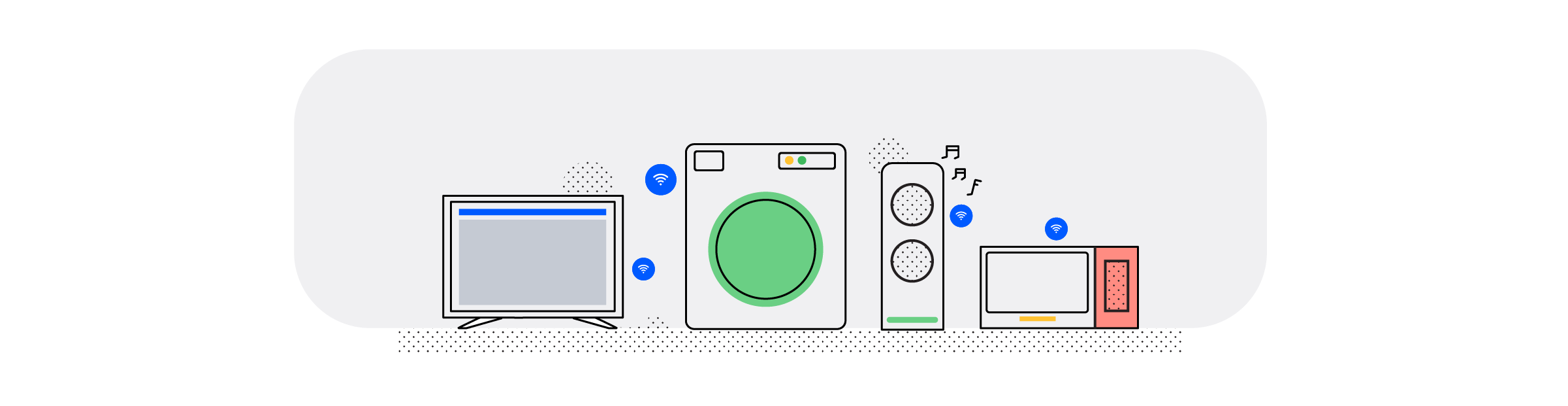
Instead of having isolated network automation, systems are bound to get more integrated as more of them enter the market.
Seeing as the big players on the market are tapping into this trend with smart TVs, fridges, door alarms, lighting systems etc., the development of the interconnected devices will move rapidly.
This is bound to bring up some privacy issues as well. Who owns the communication that flows through your devices? Do you? Or does the company that made the devices? Or someone else? How we can protect our personal privacy is something we foresee to be a big, upcoming issue.
Here are a few things to consider when you’re dealing with networks:
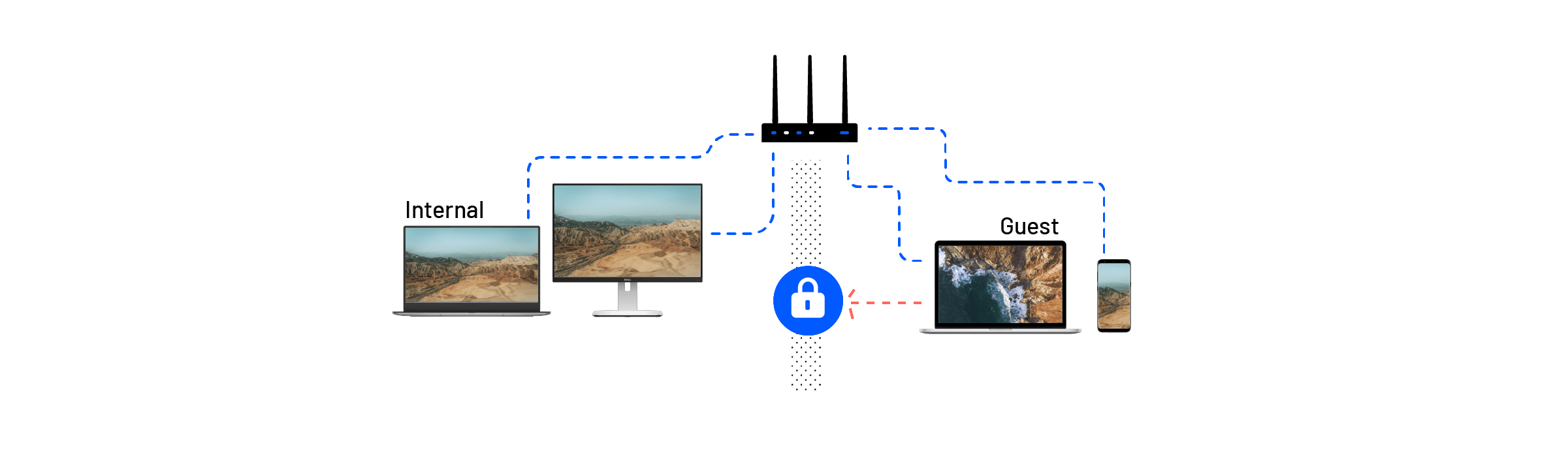
When an organization invests a lot of money in computers and other hardware, they need to protect that investment by protecting the integrity and availability of the networks.
Guests could potentially bring in malicious software (such as ransomware) on their computers that will affect the computers in the whole organization. By not merging the internal and guest networks, you’re taking the biggest and most important step towards protecting what’s in your organization.
Stay updated at all times to mitigate any potential security risks that could be lurking around the corner.
You can’t see what’s on a USB stick just by looking at the casing. It could contain malware that will seriously harm your computer and the rest of the computers around the office if you’re on the company’s internal network.
Just like you would probably think twice about putting something in your mouth that you have no clue what is, you should feed your computer with the unknown either.
When we don’t adhere to change management, things can happen and nobody will know about it before it’s too late to fix. You lose time and money when issues can’t be solved quickly, so don’t try to fix everything on your own or sweep it under the rug.